✨ Executive Summary
ZuoRAT is a Chinese-linked Remote Access Trojan (RAT) targeting SOHO routers for internal surveillance and device compromise. It leverages an ORB-style proxy C2 network where compromised routers or cloud nodes act as stealth relays. These ORB (Obfuscated Relay Backend) nodes use decoy tactics (404 pages, junk TLS certs) and support multi-purpose operations like phishing, malware delivery, and C2 relay.
The HOKAGE-GUARD operation uncovered a live, multi-functional ORB proxy network with Chinese-language panels, TLS anomalies, and clear signs of active threat infrastructure being repurposed for credential theft and RAT delivery. This report documents the infrastructure, behaviors, attribution, and defense strategies.
📊 Infrastructure Overview
Key Traits Across Nodes:
- TLS certs with junk fields (CN: defasd, Org: asde, 10-year validity)
- Self-signed certs using same fingerprint on multiple IPs
- Mix of 200 OK and 404 Not Found responses to disguise intent
- Vue.js login panels and static HTML decoys
- All nodes hosted on AS45839 (Shinjiru Technology), a known bulletproof host
Notable IPs & Behavior:
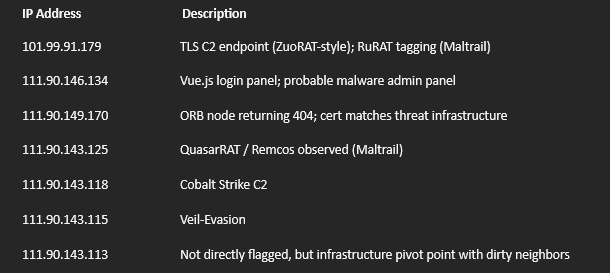
- 101.99.91.179: Static HTML decoy (nginx), valid TLS, tagged with RuRAT and APT29 (Maltrail)
- 111.90.146.134: Vue.js-based login panel, cert reuse (defasd)
- 111.90.149.170: Returns 404, but shares same self-signed cert as above
- 111.90.143.113: Not directly flagged, but neighbors host Quasar, Remcos, Veil, and Cobalt Strike
These behaviors strongly indicate a controlled and reused ORB relay network spanning malware C2s and phishing sites.
📌Validin Findings
📌 Clustering Around IP 101.99.91.179 — RuRAT + ZuoRAT Connection?
The IP 101.99.91.179 was originally flagged by our operation as a probable ZuoRAT-style ORB relay, based on its TLS certificate (defasd), self-signed structure, and infrastructure traits. However, additional OSINT and telemetry from Validin and Maltrail suggest this IP may also be associated with RuRAT, a lesser-known remote access toolkit sometimes labeled RMS, with ties to:
- Gussdoor (used in historic Chinese campaigns)
- APT29 / CozyBear TTP overlaps (per Maltrail)
Although ZuoRAT and RuRAT are distinct malware families, the infrastructure overlap, port alignment, and RAT family similarities suggest that Chinese operators may be deploying modular or forked RATs on the same ORB-style infrastructure, or leasing space across overlapping campaigns.
📍 Pivoting Through Dirty Neighborhoods — IP: 111.90.143.113
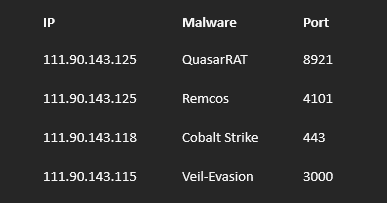
Though 111.90.143.113 isn’t directly flagged, its IP neighbors tell a different story. Within the same /28 range, we observe multiple nodes running commodity and advanced malware, including:
This IP neighborhood suggests:
- Likely shared bulletproof hosting
- Common threat actor staging ground
- Malware orchestration environments used for post-compromise control and deliver.
📌Phishing Campaigns / Malicious Infra
Chinese Phishing Alpha login page:
Suspicious Indication: Enabling Javascript
According to the virus total it indicates as malware which supports the findings with high confidence.
Algerian Embassy:
The Algerian embassy page was hosted at the time of tracking. Also reported as phishing on a platform.
Chinese Solar Power Company:
Malicious Infra Hosting on ASN: AS45839 & Default Ports
Recent Screenshots:
🇨🇳 Attribution Confidence: Moderate to High
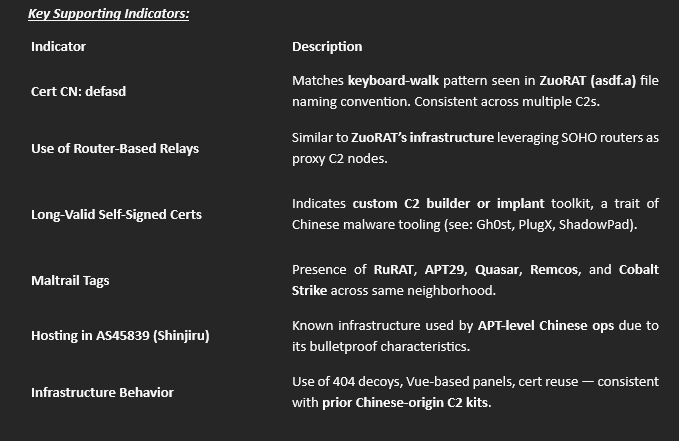
Key Supporting Indicators:
👥 Threat Actor Overlap (Possible Links)

📡 Extended Infra & Pivoting Evidence
-
101.99.91.179: Flagged on Maltrail with RuRAT, shares cert with ORB nodes
-
APT29 tagging noted (possibly reused infra or misattribution)
-
111.90.143.113: Clean IP but neighbors running:
QuasarRAT (8921)
Remcos (4101)
Cobalt Strike (443)
Veil-Evasion (3000)
This is not isolated, this is an ecosystem. This IP range is operating as a malware/phishing launchpad.
📎 IOCs
🌐 IP Addresses
TLS Cert:
CN=defasd, Org=asde, Issuer=vf, Valid: 2020–2030, SHA256-RSA, reused on all observed C2s
Ports:
443, 55556, 48101, 8921, 4101, 5651, 3000
🔗 Attribution
- CN: defasd matches ZuoRAT naming (asdf.a)
- Tool overlap with RuRAT, Quasar, Cobalt Strike, Remcos
- Shinjiru + bulletproof hosting reuse = OPSEC awareness
- Cert reuse across nodes = custom C2 builder or kit
Conclusion
The observed infrastructure forms a stealthy and reusable proxy network used for malware and phishing. Chinese threat actors are leveraging router-based ORB relays to scale and evade. Certificate reuse, decoy pages, and port diversity reinforce their OPSEC.